TunnelVision Protection for Any VPN

Recently, researchers have identified a bug in VPNs, named TunnelVision, where bad actors can take advantage of built-in features of DHCP servers (the servers that assign IP addresses) to expose and snoop VPN traffic. The researchers believe that the bug has been around since 2002 and may have been exploited since then.
The researchers suggest mitigations to secure the VPN tunnel, but most are non-starters for many organizations−such as real-time packet inspection, changing operating systems, implementing a patch to the DHCP protocol on your infrastructure, or using VMs to contain the damage−because they are resource-intensive or very hard to implement. They also disclose that even if you include firewall mitigations, those mitigations can still introduce side-channel attacks that expose new vulnerabilities.
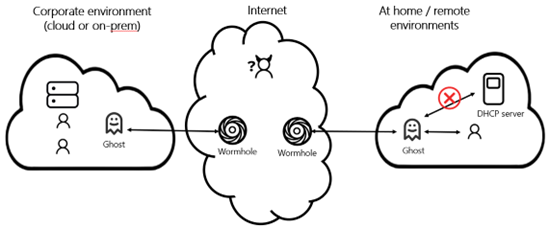
At Great Wing, we’ve developed advanced network defenses that prevent this vulnerability with our flagship DefenceDome™ Wormhole™ protocol orchestrated by the Ghost™ agent.
The Wormhole™ protocol contains packet-tampering detection capabilities so if attackers attempt to exploit TunnelVision and perform a man-in-the-middle, the Ghost™ agent will detect traffic inconsistencies, adjust to block the attacker, and reroute traffic to its appropriate destination.
Not only does Wormhole™ protocol prevent DHCP vulnerabilities, it also solves most of the problems inherent to TCP/IP by translating it to the Wormhole protocol and back again to TCP/IP. Wormhole™ turns network traffic into multiple puzzles and sends them via a very large number of messengers from many sources to many destinations.
For a bad actor to solve the puzzles, they must intercept all the pieces, arrange them in the right sequence, and know which pieces belong to which puzzle. And even if one were to reconstruct the puzzles – which is nearly impossible – it is encrypted using a very long symmetric key that changes periodically. This proprietary method for data transfer is also safe from quantum computers.
The Ghost™ translates TCP/IP into the Wormhole protocol and back again to TCP/IP. It doesn’t remain at a specific IP address or port, but jumps between IP addresses and isn’t accessible to anyone on any network. The DHCP parameters in the Ghost are automatically compiled each time the Ghost is running. Since no one can access the Ghost, no one can change the parameters.
If packets arrive from a different DHCP server on the internet, they will be blocked by the Ghost at each site on the network because of the zero-trust environment of the Wormhole, even though they are in the Wormhole protocol.
Other vulnerabilities inherent in VPNs
Two VPNs widely used today are FortiGate and Checkpoint. To protect a corporate network using these VPNs and others, you need authentication software or two-way authentication, often using your mobile phone. A bad actor who replicates remote users’ hard drives and hacks their mobile phones has full access to their corporate network, unbeknownst to them. In the hard drive, they can find the username, password, corporate IP addresses, public keys, and more.
With DefenceDome, users can continue using any VPN and the vulnerabilities mentioned above are solved once they add DefenceDome to their system. Even if a bad actor succeeds in replicating a user’s computer and hacking their phone and has access to text messages, emails, usernames, and passwords, the bad actor still cannot access the corporate network.
DefenceDome also provides:
- Zero-trust environment
- Protection from Denial of Service (DoS) attacks
- Protection from eavesdropping
- Protection from any direct attack on the corporate servers (because they don’t have internet access with our solution)
- Quantum-resistant encryption
- Secure VPN-like pathway
- Reports of attempted attacks
To learn more about DefenceDome technology and how it can protect data in transit for any network without the need to change the network infrastructure, software, or tools contact info@greatwing.com.
